
Phishing Scams 3.0 Are Exploiting Legitimate Services, Be Careful
 By Cinthya Alaniz Salazar | Journalist & Industry Analyst -
Thu, 04/06/2023 - 09:30
By Cinthya Alaniz Salazar | Journalist & Industry Analyst -
Thu, 04/06/2023 - 09:30
Check Point Software 2023 Cybersecurity Report indicates that threat-actors are increasingly exploiting legitimate services to conceal malicious payloads. The evolving sophistication of “phishing scams 3.0,” through which attackers use legitimate services, has led to a spike of business email compromise (BEC) attacks, comprising 86% of all file based in-the-wild attacks.
“BEC is one of the most damaging and expensive types of phishing attacks in existence. While ransomware tends to attract more notoriety, the FBI reported that BEC-related scams totaled US$2.7 billion in 2022, compared to just US$34 million for ransomware,” according to a Check Point press release.
Business email compromise is a specific type of phishing attack, a spear phishing attack to be precise, that aims to trick employees into taking harmful actions, typically sending money to the attacker. Consequently, their new found ability to impersonate legitimate firms and services makes phishing scams 3.0 much more dangerous. With this in mind, the cybersecurity company has advised users “to remain cautious and be aware of links within any email, including those coming from known vendors and services.”
This type of attack emerged in 2020, attempting to trick recipients into thinking that the email originated from senior executives in a firm making legitimate financial requests, such as payments for services or vouchers. In other words, this scam relies heavily on its ability to appear genuine and from someone of authority so as to not raise suspicion. Moving on from internal sabotage campaigns, scammers have opted to impersonate legitimate, popular firms and services like PayPal and Google Docs to gain entry into a user's inbox.
Examples:
Does this type of email look familiar? In the following picture, the hacker added a comment mentioning the intended target in Google Sheets with a proxy account so they receive an email notification.
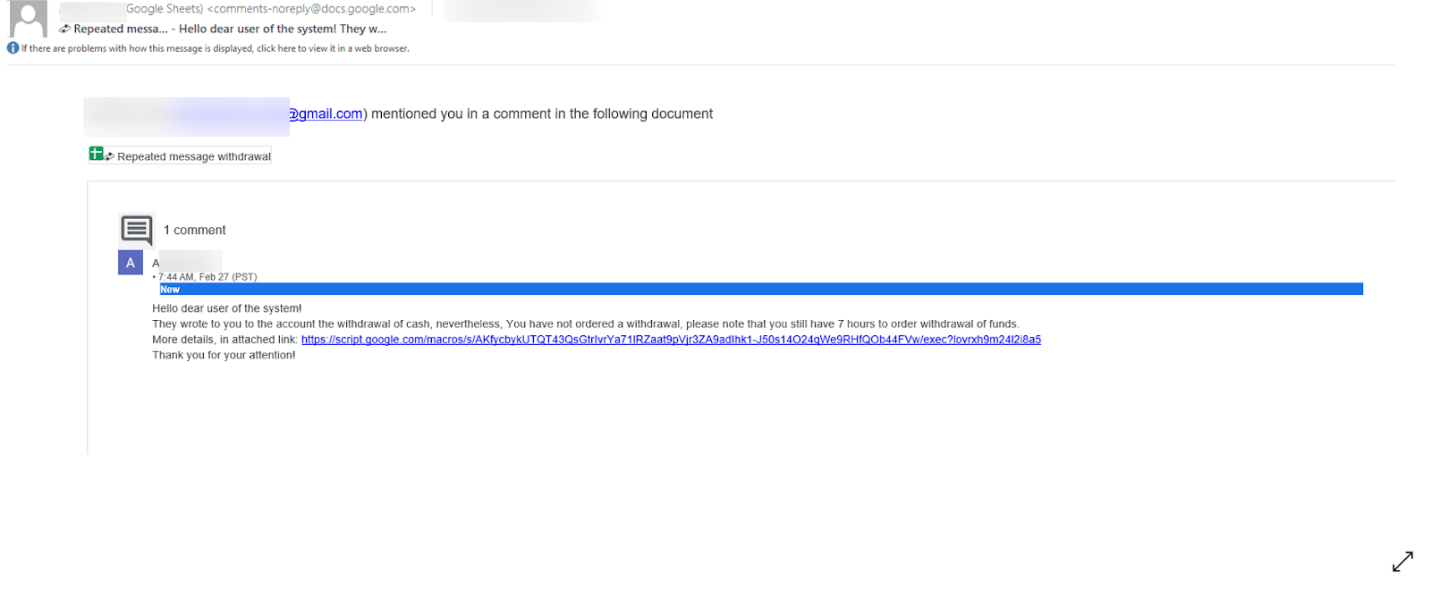
From there, if a user is successfully deceived, the URL will redirect them to a fake cryptocurrency site which can be used to different ends including stealing credentials, theft or crypto mining.
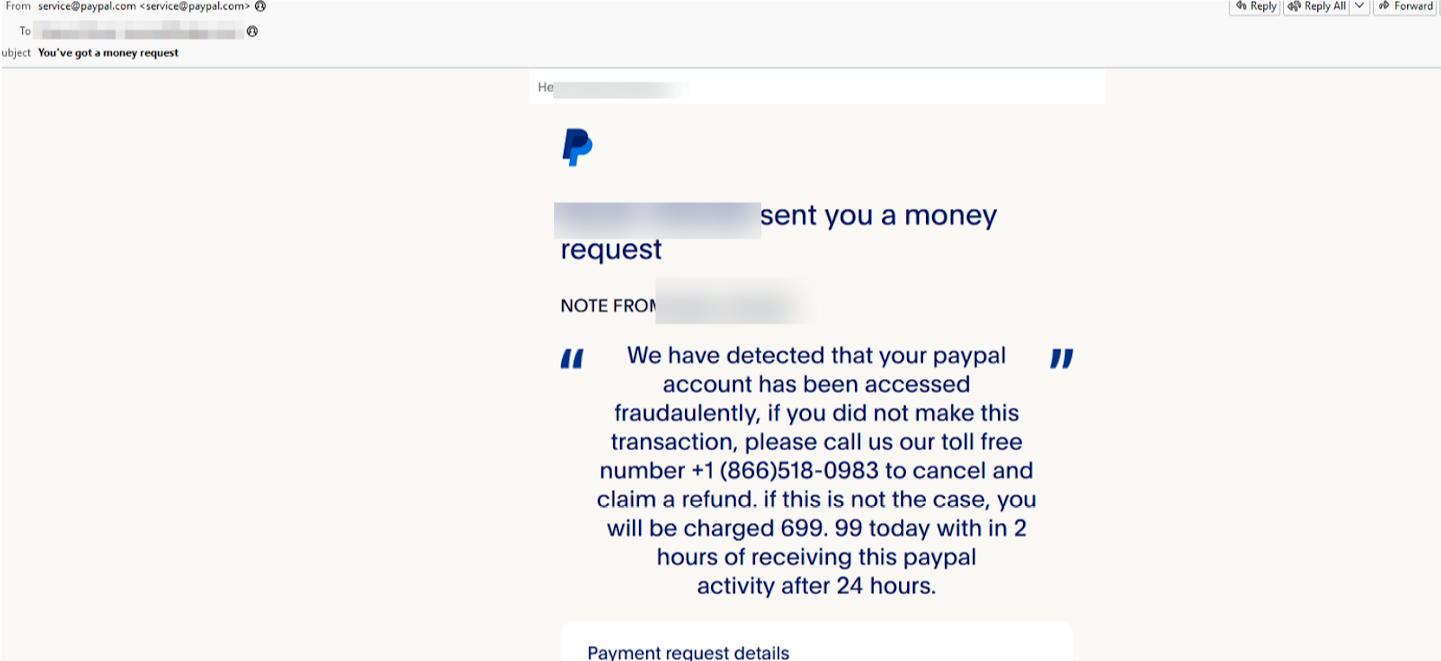
“In all examples recorded, the email address from which the email was sent looked perfectly legitimate and contained the ‘correct’ addresses, which makes detection and identification much harder for the average user receiving them,” according to the report.
To protect against these attacks, Check Point Software suggests taking a few precautions to avoid potentially costly and damaging BEC attacks including adopting anti-phishing protections, investing in employee education, instituting two-person verification protocols and labeling external emails.
















